Cryptography essentially runs data through a program that will muddle up all of the data in such a way that it is unreadable. This is done with a "key". You can use one key to encrypt the data and another to undo the operation. Usually for data security means, this key is a private key that only you will be able to use to undo the action, however for information such as websites and stores, Public keys can be used. This public key infrastructure doesn't entirely get rid of private keys but will use one master key to encrypt it and will require a single public key to undo.
To understand the fundamental features of cryptography, we must understand why and how we would use these in the real world.
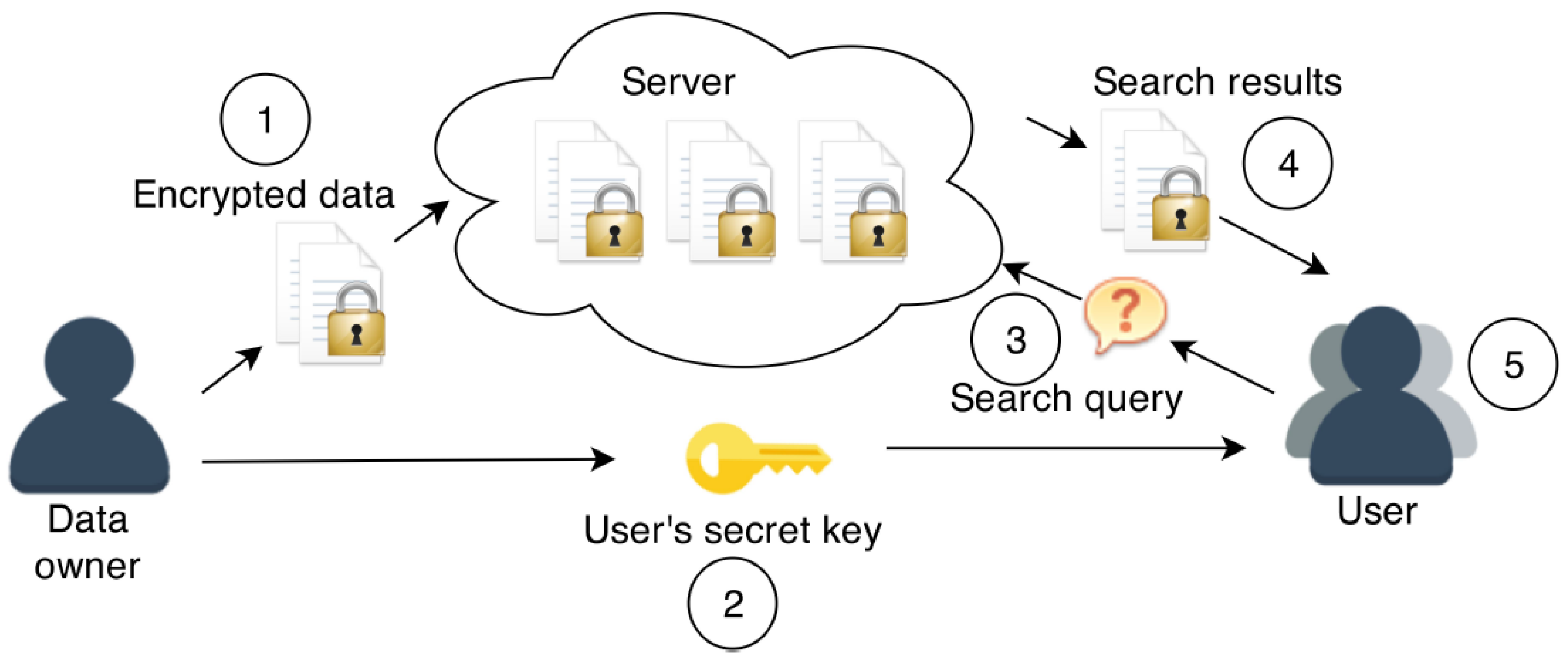 As most of this data is flowing through a "public forum" or public space, we may not want everyone to read this data. we use encryption for this.
As most of this data is flowing through a "public forum" or public space, we may not want everyone to read this data. we use encryption for this.Much like the Enigma code used in WW2, we would run Plain text (normal, readable text) through, this would use a Encryption key & Encryption program to secure this, send it through. At this point the idea is that the message will be completely illegible and unreadable (or "hashed) and the end user would need the decryption key and decryption program to make this legible again. This was used in practise to keep messages meant for German soldiers inaccessible to the British, for example, if they widespread the message in Plain text, it would difficult to protect that message and make sure nobody else could read it, so the enigma code was given to select trusted soldiers and released the messages publicly, knowing that the British couldn't read them.
Hashing, whilst not unlike encryption is another way to protect your data. Hashing is more of a one-way encryption where is usually reversible.The best hashing algorithms are designed so that it's impossible to reverse the procedure. To do this, "Salt" or random data is added to the code so that it can only be encrypted one way.
Hashing is especially handy for passwords. you would store the password by hashing it with a salt (so that it can not be undone, but it is hashed), and hash the password when it is typed in. If the two hashed results are are similar, you can be sure that it is the correct password without it reading the "actual" password. Another use case for this could be credit card details. As you would not want to send these over in plain text (as someone might read them) you would hash them, and use the hashed result as the comparison.
We would always want to use this in a public space as people who have access to this, may eavesdrop or even worse, change this message to something perhaps more destructive than originally intended.
This does also provide us with confidentiality at the same time.

The secrecy in modern day usage is based upon keeping the encryption and decryption keys (whilst often the same, or "symetric") safe and out of the hands of others, whilst HTTPS uses both simultaneously.
Symetric encryption is the best known and oldest form of encryption. The idea is that you can run the message with the key and encrypt it, and you can use the same key in reverse to get the message. This requires both the end user and recipient to know the key to do this, and if the key is compromised, your message might be readable to others.
Asymetric (or public) keys are keys that are essentially different as they are released. In the sense that a public key would be used to encrypt the data and made publically avaliable for anyone to send you a message, whereas the private key would be used to decrypt the data and kept safe.
Data integrity can be assured by adding hashes to encrypted messages. This is done with HMAC (Hashed message authentication code) so that a password must be used to remove the hashed code correctly as well as needing the key to decrypt the message. Doing this you can ensure that the message has not been changed or altered.
Non-repudiation is derived from repidiation, which means to deny, so non-repudiation is to prevent denial. This means that users cannot deny that they recieved the message or it's validity, for example recieving an order placed email from Amazon, they would have their digital signature and unique details on the email to one, prove it was meant for you, and two, that it was Amazon who sent it.
Email tracking can also help with this, as looking at the email details, you will be able to see which email server sent the messages and which email server it was delivered to, proving that amazon sent it and that the recipient received it.
Access control is used to make sure that the users who have the correct unique key are only able to open the file, and that using an incorrect key will not allow access to the file. This can be done using HMAC as stated before, will password protect the file as well as encrypting it with a key.
Public key infrastructure (PKI) is a set of rules and policies to create and distributes digital certificates and keys. This is done with asymetric keys, in the form that the consumer will use the public key given freely to encrypt their documents, and the authorative company or indivdual will provide the private key to decrypt information they are sent. A certification authority (CA) will authorise and give out the keys to individuals or companies, much like an authorative government will distribute ID cards or passports, and because your documents are signed and authorised by this CA, you can use this certificate to prove identity.
Key management is an important step with encryption keys, and is nessecary to control how these keys are used. Like many things, keys will have a lifecycle where they are created, used, retired and then destroyed.
Every so often, as private keys can be found, it is wise to change the keys to keep your security up and prevent people trying to crack the code over time. Browsers using the HTTPS tag will be given a key by the website it is browsing, the server being accessed will automatically generate a key for them to use. The lifetime of these keys is based on a number of factors such as the sensitivity of the data thatis being used, the purpose of the key and how much data is being protected.
Keys are usually created using a key management system, or by third party providers.
If for any reason they believe that the key is compromised or the had changed ownership, they key will have to be expired earlier and a new one created. The GDPR has been put in place and regulated that no large company can ignore data protection, hence encryption has become commonplace.
Authenticity in encryption is making sure that the message leads to the correct people and that only they are able to unlock the message being sent across. This can be done with private keys that have been shared between both parties or another similar key form.
Read more here: https://economictimes.indiatimes.com/definition/cryptography
Read more here: https://www.khanacademy.org/computing/computer-science/cryptography
Read more here: https://www.britannica.com/topic/cryptology
Read more here: https://www.cryptomathic.com/news-events/blog/exploring-the-lifecycle-of-a-cryptographic-key-
No comments:
Post a Comment